Technology
UCSC students discover, help patch cybersecurity flaw for free laundry
UCSC students worked with the company that provides the app and the machines, called CSC Serviceworks, to help patch the cybersecurity flaws that could let millions of customers run loads of laundry for free.

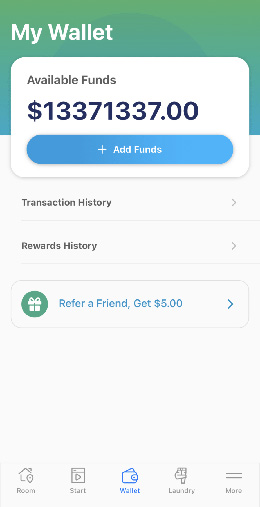
UC Santa Cruz first-year computer science and engineering student Alexander Sherbrooke was starting up a late night load of laundry at Porter College when he started wondering about the security of the internet-connected machine in front of him. Pulling out his computer, he realized he could tap into the machine’s public-facing application programming interface (API) and run a script of code that told the laundry machine to start a load, even though he hadn’t yet paid the necessary one dollar fee.
Immediately curious about this vulnerability in the laundry machine’s interface, he took his discovery to Slug Security, a club for students interested in hacking and cybersecurity. Working with Slug Security vice-president and second-year computer engineering student Ex Taranenko, the two students soon discovered that beyond just being able to start loads for free, they could manipulate the machines to add obviously ridiculous millions of dollars to their digital wallets in the app used to pay for laundry.
Now, the students have worked with the company that provides the app and the machines, called CSC Serviceworks, to help patch the cybersecurity flaws that could let millions of customers run loads of laundry for free. By reporting the error to the company, the students engaged in the cybersecurity process known as “ethical disclosure,” helping to protect against attacks by true bad actors.
“I don’t feel like I’m the sort of ‘hacker’ to the level of the Slug Security club leaders — I was simply curious about the inner workings of the things we use every day and learned the tools required to dig deeper,” Sherbrooke said. “I think it’s awesome that anyone can discover a vulnerability, no matter how skilled they are.”
The security vulnerability was on the part of CSC ServiceWorks, a laundry service company that provides more than a million machines at university campuses, hotels, and residences in the U.S., Canada, and Europe. Shortly after discovering the flaw in mid-January, Sherbrooke and Taranenko began the process of ethical disclosure, reaching out to the company directly to make them aware of the bug.
After trying multiple avenues to get in touch with the company with no response, the students moved forward with submitting a disclosure to the CERT Coordination Center, which helps independent security researchers get in touch with vendors and provide solutions to bugs.
“Companies should assume they will get attacked,” said Baskin Engineering Associate Professor of Computer Science Alvaro Cardenas, who advises the Slug Security club. “They should have a vulnerability reporting process so they can receive information from vulnerability researchers and a process to patch their software to prevent future attacks.”
After waiting longer than the normal three months for a response, the student researchers decided to publicize their discoveries. Without publicly disclosing this vulnerability, other attackers could have found the same problem and exploit the vulnerability in secret. Even though providing free laundry for college students may not seem like the most disastrous of consequences, they knew that having heavy machinery vulnerable to the influence of outside actors could create problems. For example, the students weren’t sure if the safety commands that prevent modern laundry machines from overheating and catching fire could be bypassed via the API — although the machines at UC Santa Cruz have built-in temperature limit switches.
Sherbrooke and Taranenko reached out to a journalist at the publication TechCrunch, who wrote a story on their discovery. This public-facing exposure of the security flaw seemed to be the trigger that CSC ServiceWorks needed to get in touch, as they then reached out to the students and Cardenas for their feedback and input. The students met with representatives from the company, who told them that they were working on solutions to the flaws that had been uncovered.
At this point, CSC ServiceWorks seems to have fixed the bug that enables the machines to start for free, but not the one that allows people to add limitless amounts of money to their digital wallets. The company noted that they have to be careful not to deny service to existing customers in the process of updating the API to make it more secure, so patching the issue could take some time. In the meantime, they have added more robust contact information to their website for easier communication should further cybersecurity issues arise.
Building on the exciting experience of working on real-world cybersecurity flaws, Sherbrooke and Taranenko are running ethical disclosure workshops at Slug Security to help other UCSC students learn more about the processes of reporting vulnerabilities.